In response to demand from security-conscious OEMs, the manufacturers of modern microcontrollers and systems-on-chip (SoCs) commonly equip their products with a broad range of security capabilities: standard, off-the-shelf 32-bit MCUs for mainstream, non-financial applications will today often feature a hardware cryptographic accelerator, a random number generator (RNG) and secure memory locations.
But serial Flash memory – the location in which much of an OEM’s precious intellectual property (IP) is stored – has traditionally been more vulnerable than the SoC or microcontroller. Security weaknesses in the companion Flash memory to an MCU or SoC expose OEMs to the commercially damaging risk of product theft due to the cloning of reverse engineered PCB designs. This article explains how Authentication Flash can be uniquely and securely paired to an authorized host controller.
A fundamental security requirement for every reputable OEM is to prevent the possibility of theft or cloning of the OEM’s IP, including application code that is stored in external serial NOR Flash.
Of course, much of the value embedded in an electronics end product is not secret. Take the example of a smart home Internet of Things (IoT) thermostat: a painstaking tear-down analysis of the thermostat’s board assembly will enable all the components to be precisely identified and the board layout to be faithfully replicated by any factory that wishes to clone the product. The hardware design is not secret.
The application code is secret – or rather, it ought to be. An electronics system, however, is only as strong as its weakest link. Today, the main SoC or MCU is normally strongly protected by encryption, anti-tampering and secure storage capabilities implemented in hardware and software. So if an attacker wishes to clone the product’s application code, it’s most likely entry point is an external Flash memory IC.
For this reason, OEMs today commonly ‘protect’ their code storage hardware with a unique identifier (UID) stored in partitioned memory space in the Flash IC. In truth, however, a UID offers only a trivial barrier to attack. Any engineer with some security knowledge will be able to locate and identify its UID and easily disable the pairing between the MCU and code storage hardware. Once the pairing is removed, the OEM’s root of trust is broken. The code stored on the device can be copied, and cloning of the thermostat design can begin in earnest.
The weakness in this Flash security system is that the UID itself is not secure. It is a permanent, unchanging code number: once read out of memory, it can be used again by a non-authorized host.
The solution: secure, dynamic authentication
The remedy for this problem is easy to design in theory: the UID needs to be different every time the memory is challenged by the host. But the advantage of the fixed UID used today is its ease of implementation: it just needs to be programmed once into the Flash memory, and once into the host controller; then the two values may be simply compared to authenticate the Flash device.
So how can the response to a challenge from the host be different every time, yet still recognized by the host?
Symmetric encryption of memory ID
This is the problem that Winbond has set out to solve with its W74M family of Authentication Flash ICs (see Figure 1). Winbond is best known for its broad portfolio of serial NOR and NAND Flash memory ICs: it is the world’s top producer of serial Flash, with around a 30% share of the market. In 2016, Winbond shipped 2.1 billion units of its SpiFlash® serial Flash ICs.
It is now also addressing the issues that customers face with security vulnerability in the Flash memory portion of their designs: this is the reason for the introduction of the W74M family. The basic method by which Winbond secures a memory’s identity is through symmetric encryption: both host and memory know the same secret, a ‘root key’.
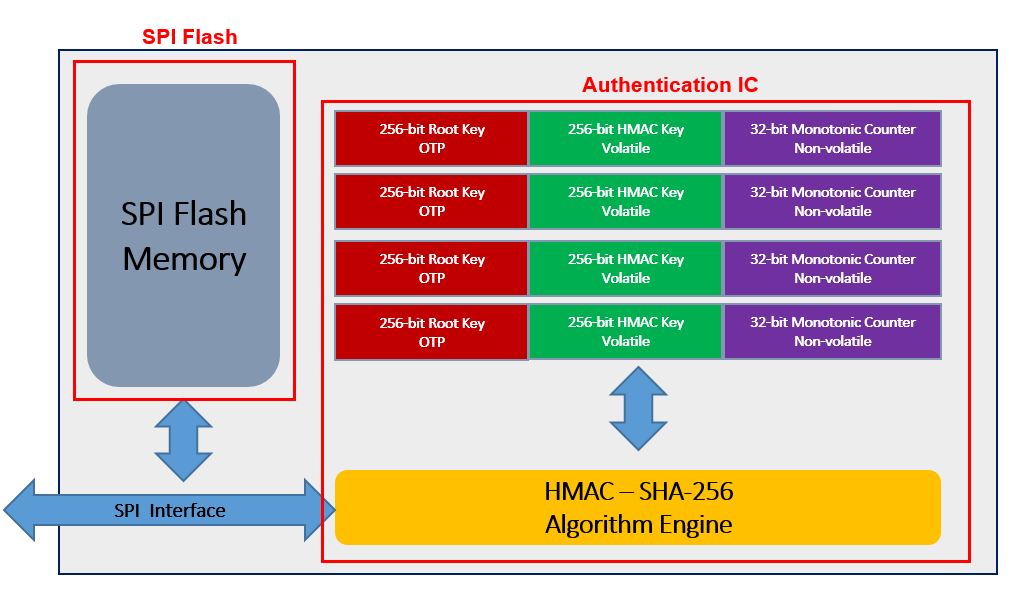
Fig. 1: the architecture of the W74M multi-chip package
The root key is, however, never directly transmitted between host and memory (the ‘challenger’ and ‘responder’). Instead, an encrypted message (a Hash-based Message Authentication Code, or HMAC) is generated by a combination of the root key and a dynamic element such as a random number; this combination is then processed through an encryption algorithm, the SHA-256. SHA-256 stands for Secure Hash Algorithm with a digest size of 256 bits – a cryptographic hash function published by the US National Institute of Standards and Technology (NIST) as a Federal Information Processing Standard (FIPS). It is a cryptographic function used for processing financial transactions, and is generally considered to be unbreakable in practice.
To authenticate the W74M memory, the host controller compares the value of the memory’s HMAC against the value it computes by use of its root key and the same random number processed through SHA-256. If the values match, normal memory operations can proceed.
Because the HMAC is generated in part by a dynamic element, such as a random number, the value of the HMAC is different every time it is generated. This means that attacks which succeed against a Flash memory with a conventional, fixed UID, as described above, will fail when made against a W74M memory. And because the SHA-256 function is so secure, there is in practice no risk that an attacker will be able to decrypt the HMAC to reveal the value of the root key.
Figure 1 also shows two other interesting features of the W74M. First, the non-volatile monotonic counter provides a supplementary verification of the memory’s authenticity. The counter starts at zero when the root key is established, and a single increment is added in response to a command issued by the host controller, meaning that the counter has a unique value known only to the memory and the host. If the counter value provided by the memory when challenged by the host does not match the host’s counter value, the value of the memory’s HMAC will not be the same as that computed by the host: this signals to the host processor that the W74M authentication device has been tampered with.
The processor can use this knowledge to protect the host system, for instance by preventing the device which has been tampered with from gaining access to the host system’s resources. This protects against the risk that an attacker replaces the W74M unit mounted to the board by the OEM with a different W74M in order to hijack it.
This protection capability is relevant to the second feature of note shown in Figure 1: there are four instances of the combination of root key/HMAC/monotonic counter in each W74M device. One instance will be used for authentication of the host device’s controller. The other three authentication ‘channels’ are intended for use for example in IoT devices which have to verify their identity in order to gain access to networked services (see Figure 2). As shown here, a different root key can be securely stored for each authentication channel, and shared with the relevant host device. This means that the root keys of the host device, of the internet gateway and of the cloud service remain secret: one device has no knowledge of another’s root key.
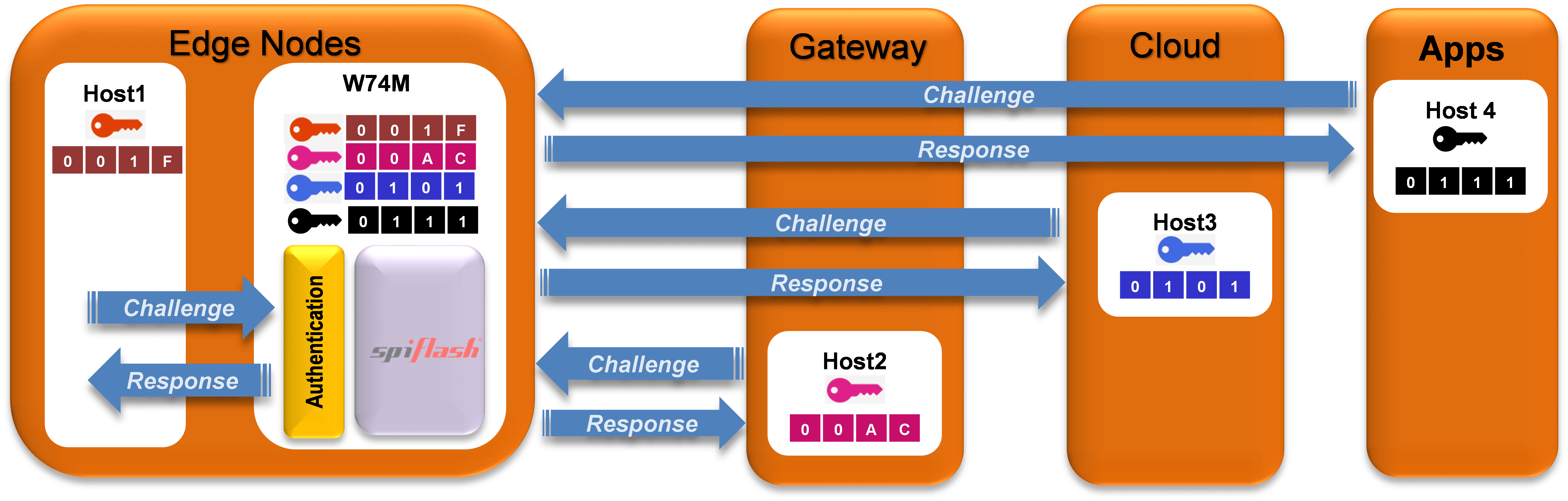
Fig. 2: multi-layered authentication enabled by the W74M
Another use case for this multi-layered authentication capability is in a complex system such as a drone, which is composed of multiple elements. A W74M device in one of these elements may be used to authenticate:
- the drone’s main processor
- the removable battery module
- the remote control
- a camera
Secure, encrypted authentication enables the drone manufacturer to ensure that only branded cameras and branded replacement batteries may be used, and prevents the possibility of an unauthorized remote control hijacking the drone in flight.
Safe and secure implementation
As described above, the W74M’s cryptographic functions are extremely secure. In addition, the root keys are stored in OTP memory space which cannot be read by an external device.
The W74M device itself, then, is inherently secure. Secure implementation also requires secure provisioning, to ensure that the root keys programmed into each W74M unit and host SoC or controller in production remain a secret of the OEM. This normally depends on the OEM’s own provisioning and production processes, although Winbond can optionally take care of root key provisioning of the W74M on a customer’s behalf.
The W74M family of authentication Flash devices is available in various densities from 32Mb to 1Gb, in standard packages. This means that secure device designs which today incorporate a NOR/NAND Flash IC for code storage and an external authentication IC can replace these two chips with a single W74M package that fits in a standard Flash socket, offering a bill-of-materials cost and component count reduction while providing the most secure level of authentication.
The W74M is also available as a pure multi-layered authentication device with no NOR Flash memory capacity, as the part numbers W74M00AVSSIG and W74M00AVSNIG.
By CS Lin, Marketing Executive, Winbond Electronics Corporation America
For more information about product, please visit Winbond Authentication Flash.


 English
English